
Many large enterprise organizations are adopting the Zero Trust Security Model for their network architectures. The Zero Trust Model is a concept that suggests organizations should not automatically trust anything inside or outside their network perimeters. There is no single set of controls that will achieve Zero Trust. However, as described by the model, there are specific factors that need to be considered in order to design a Zero Trust Architecture (ZTA). These factors are as follows:
- User Verification
- Multi-factor authentication (MFA)
- Device validation
- Device certificates
- A/V signature updates
- Latest applied patches
- Access control (least privilege)
- Policies
- Segmentation and sub-segmentation
In the case of Industrial Organizations, their networks not only contain IT but also OT (Industrial Control Systems and Internet of Things) devices as well. Securing an IT network is vastly different than securing an OT network in terms of available protections. Therefore, the Zero Trust approach for the OT network will be different from the approach for the IT network. After thorough research, Anvaya Solutions security experts developed a highly secure model for organizations to secure their OT environments.
The model took into consideration multiple case studies of Industrial Control Systems (ICS) related security incidents, such as Stuxnet, the Ukrainian Power Grid Attack (2015), and other such critical infrastructure within the U.S as well. These incidents introduced a change in the cybersecurity mindset to consider OT network security as part of organizational security. Case studies by leading security experts and organizations contend that these incidents could have been prevented by implementing proper segmentation. These experts universally suggest complete separation of the OT and IT network, per the Purdue reference model for ICS network segmentation as shown below:
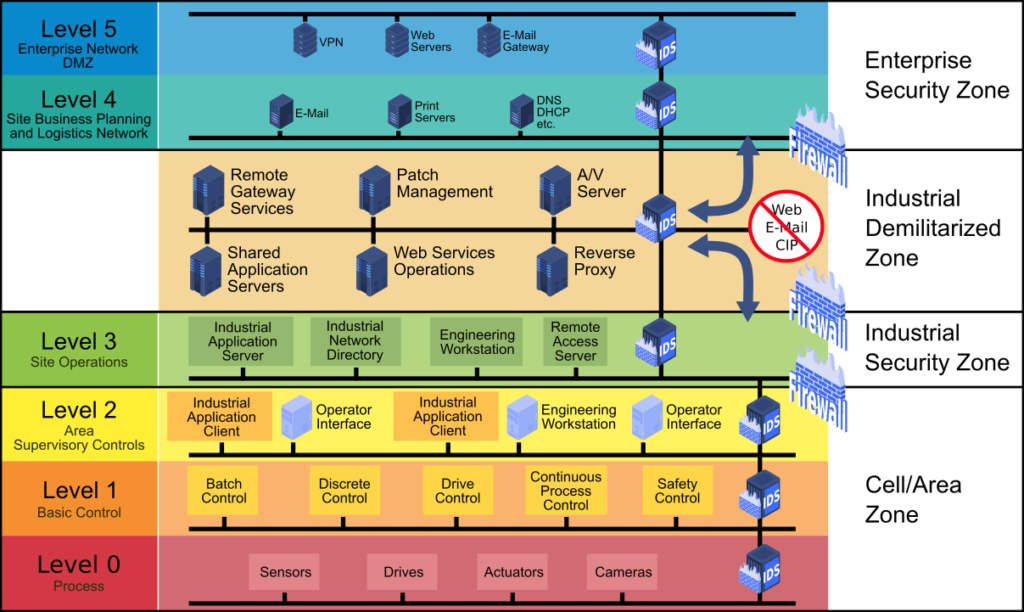
Modified to reflect NIST SP 800-82 guidelines
The Purdue reference model was designed as a resource to help design an ICS network architecture. The model makes use of zones to subdivide an Enterprise and ICS network into segments based on the similarity of functions and/or requirements.
- The enterprise zone is part of the ICS where Enterprise Resource Planning occurs.
- The industrial demilitarized zone (IDMZ) is an information-sharing layer between the IT and OT systems that acts as an extra layer of separation to minimize the risk of exposure of lower layers to direct attacks or compromises. In the case of a compromise, the IDMZ can be easily shut down, allowing the ICS systems to continue operations as well as contain the threat.
- The industrial security zone, also known as the manufacturing zone, is where the ICS systems responsible for control management operate.
- The cell or area zone is a functional area within an ICS facility. It is recommended that each level in this zone is also secured appropriately.
The SANS Institute, the largest and most trusted source for information security training in the world, proposes a multi-layered defence in depth for ICS networks, shown in Figure 2 below, to protect each level identified in the Purdue reference model.
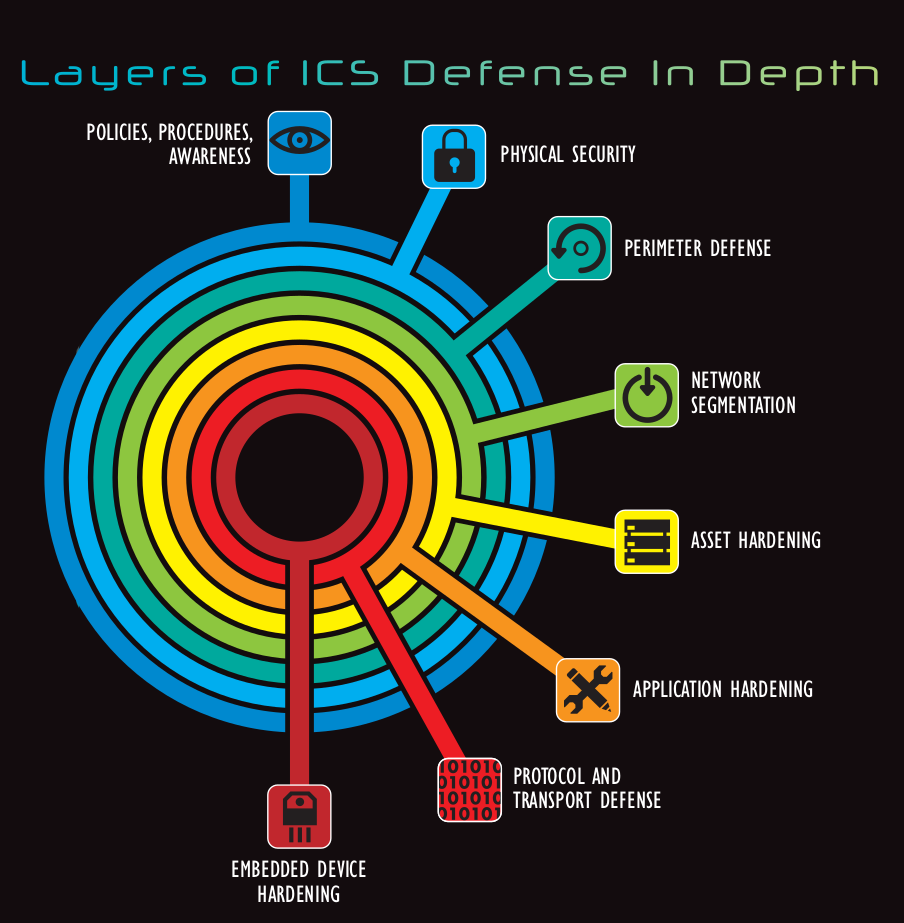
According to NIST Special Publication 800-82 Rev. 2: Guide to Industrial Control Systems Security, “network segmentation is one of the most effective architectural concepts that an organization can implement to protect its ICS.” Segmentation is aimed to “minimize access to sensitive information, ICS communication and equipment, and make it significantly more difficult for an adversary.” [Ref. 1]
The security model created by Anvaya Solutions considers all of the above industry guidelines as well as the following key points as important factors while designing the security for OT networks:
- Business needs
- Network communication
- Firewall
- Encryption
- Who or what needs access
- Access Control
- Packet forwarding
- Content filtering
- Traffic monitoring
- Intrusion Detection and Prevention Systems
- Activity monitoring
- Future proof network
There are multiple caveats an organization needs to consider when dealing with OT environments. One of such caveats is that ICS devices utilize different communication means and have different operating systems that may not have the capability to support the ZTA requirements.
Considering these factors, it is almost impossible to implement ZTA for ICS networks with the same network devices that are used for IT. Research shows that Software Defined Network (SDN) is potentially a better option for ICS to achieve their security goals and prepare for ZTA. SDN separates the control logic from routers and switches, leaving them to forward traffic between devices. By centralizing control logic, SDN will make the network programmable, automating the ICS network and simplifying policy enforcement. This is essential in both future-proofing the ICS network and enabling the implementation of the aforementioned ZTA key factors for such networks.
Additionally, incident response is an important part of any ICS security. Since ICS systems often have different operating systems and technical caveats, the ICS incident response will differ from the IT response; there is no log collection in ICS devices to utilize a Security Information and Event Management (SIEM) tool and ICS systems cannot be taken offline as a corporate workstation would in the case of an incident. Deployment of SDN can help with automating incident response processes by providing better control over traffic flow across the ICS network.
Anvaya Solutions security team can help your organization in the design of ZTA for the OT environment.
Schedule a complimentary cybersecurity consultation with the experts at Anvaya Solutions and learn how Anvaya can start helping your organization enhance your security posture with pro-active cybersecurity.